CircleCI is a continuous integration and delivery platform that helps organizations automate application delivery with faster builds and simplified pipeline maintenance. CircleCI in particular offers the ability to automate testing during the CI/CD process as part of their daily team habits.
CircleCI jobs require secrets in order to pull code from Git repo (e.g. GitHub token) and for installing this code on a newly defined environment (e.g. CSP credentials – access key). By integrating CircleCI with Akeyless Vault, you would not need to keep hard coded secrets within the CircleCI jobs such as API-keys, tokens, certificates and username & password credentials.
With an Akeyless Vault integration to CircleCI, Akeyless acts as a centralized secrets management platform by efficiently provisioning user secrets into CircleCI jobs. Akeyless handles secret provisioning through injecting Static or Dynamic Keys into CircleCI jobs. While doing so, Akeyless leverages existing CircleCI functionalities such as jobs, workflows, contexts, in order to securely fetch secrets to CircleCI pipelines.
Benefits of Using a Centralized Secrets Management Solution
With a centralized secrets management platform like Akeyless Vault, CircleCI and all other DevOps tool’s secrets are unified and secured. A secrets management platform like the Akeyless Vault makes it operationally simpler to maintain compliance and generate secret access reports with a usage visibility of what secret, when accessed, and from where.
Operation-Wise – For an organization with multiple DevOps tools, managing secrets becomes complicated and requires considerable effort to maintain workforce efficiency. With a holistic secrets management platform like Akeyless, an organization maintains a single source of secrets into different DevOps applications and workflows simultaneously.
Audit-Wise – With a consolidated audit of all application secrets directly through the Akeyless Vault, an organization can ensure audit compliance centrally instead of auditing multiple secret repositories.
Functionality-Wise – Most DevOps tools, including CircleCI, lack the Zero-Trust strategy while administering secrets. A centralized secrets management solution like Akeyless, secrets are generated on-the-fly to fetch into CircleCI jobs Just-in-Time, thereby aiding a Zero-Trust posture.
Security-Wise – Through Akeyless, CircleCI job secrets are provisioned through Static and Dynamic Keys instead of the default way of storing secrets as plain text. Additionally, with automatic expiry of SSH Certificates, Akeyless avoids abuse and theft of access privileges.
How to Fetch a Secret with Akeyless Vault in CircleCI
With benefits like ease of operation and enhanced security allowed by Akeyless Vault’s centralized secrets management platform, let’s go through the simple steps to fetch a secret in CircleCI.
Prerequisites
1.You need to have an existing repo that is followed by CircleCI (in our example it’s named TestRepo):
2. Sign In or create an account with Akeyless (it’s free) by accessing the URL: https://console.akeyless.io/register
3. In case you are a new user, create your first secret in Akeyless as shown below:
Configuration
1. Setup global configuration in your CircleCI project
a. Go into Project Settings:
b. Go into Environment Variables to setup global configuration:
In our example, you would need to configure the following environment variables:
- · api_gateway_url
- · admin_email
- · admin_password
If you have your own Akeyless API Gateway setup – set the URL for the Restful API, otherwise you can use Akeyless Public API Gateway with the following URL:
Similarly, set your admin_email and admin_password as environment variables:
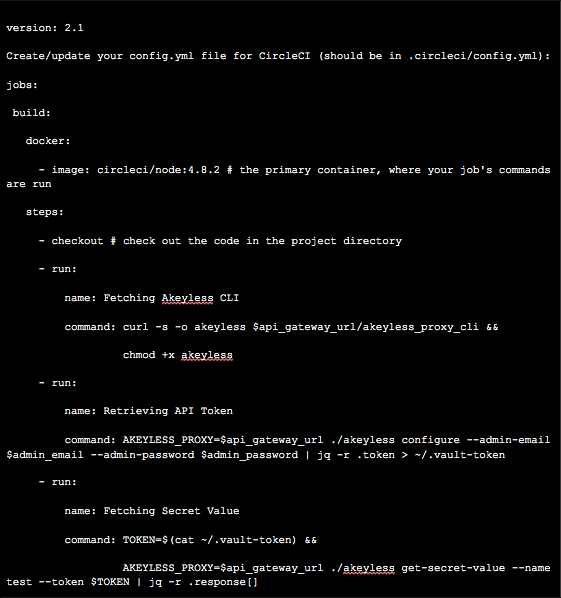
2. Create/update your config.yml file for CircleCI (should be in .circleci/config.yml):
3. Pipeline will be triggered and you’ll be able to view your build:
To Sum Up
With the Akeyless Vault plugin for CircleCI, an organization can manage CircleCI secrets effortlessly, cutting down operational hassles in addition to maintaining security. With the use of Static or Dynamic secrets, access policies are efficiently permission-controlled across multiple layers of a DevOps workflow.