Brute force attacks are most common attacks used by hackers. This type of attack has compromised many online user credentials.
Hackers are using brute force attack to target any website they could get, ranging from Fortune 500 companies to very small websites.
The aim of such attacks is mainly to compromise user information (including Social Security numbers, credit card data and bank account details) and commit financial frauds using identity theft. Once information is obtained by hackers it can be misused by them for selling in black market, spamming and more unethical means to exploit it.
In this article we are going to discuss the use of graph database for stopping the brute force attack.
What Is Brute Force Attack?
In cryptography, Brute force attack is defined as a approach of systematically checking all possible passwords until the correct one is found. This type of attack may take time proportional to the complexity of password.
Brute force attacks are typically performed with the help of dictionary containing most common usernames, passwords and english words and variants.
For example some of the most commonly used passwords are listed below
- 123456
- password
- 12345678
- qwerty
- abc123
and most common user names are
- admin
- root
How To Identify A Brute Force Attack Is In Progress?
There can be multiple approaches to identify brute force attacks.
- Most common way is to track failed login attempts. If there are many failed login attempts from an IP within short period of time it may be sign of a brute force attack.
- Too Many Login attempts with easy passwords that are not allowed on website. This can be a easy catch for your website since in case your password policy does not allow easy passwords. An easy password list can be maintained for identifying attack is being made with a password dictionary.
How Neo4j Can Help In Detecting Brute Force Attack?
Neo4j is a highly scalable graph database where multiple complex relations can be easily stored and retrieved. The ability to do complex query in real time can prove really helpful in identifying a brute force attack must faster.
We have used Neo4j 2.1.4 in this article, however this should be achievable with any version of Neo4j and other popular graph databases.
Information To Capture In Neo4j Graph Database
The most important thing to do in identifying such attacks is to capture enough information about each request. Some of the required information is
- Client IP Address – Remember to get the real client IP address not proxy IP.
- Login Attempt Success or Failure information
- Timestamp
Setting Up The Structure Of Graph
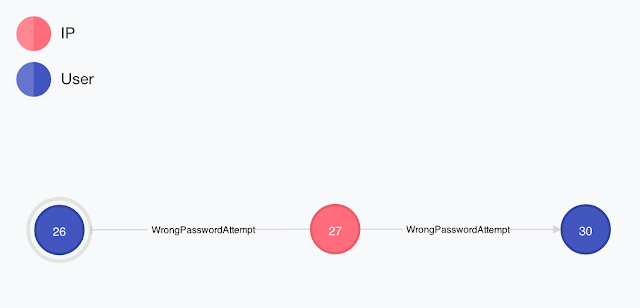
The graph structure for this is going to be really simple with just 2 types of nodes and 1 type of relationship
- User Nodes
- IP Nodes
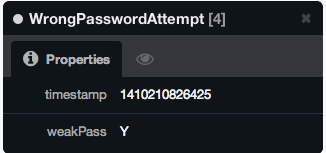
- WrongPasswordAttempt Relations (with two attributes timestamp & weakPass)
Neo4j Cypher Queries To Create The Graph
Neo4j database uses Cypher query language to manipulate data on Neo4j. Below are some queries you can use to setup and retrieve data from graph database.
Create unique constraint on the attribute value level to avoid any duplicate nodes.
CREATE CONSTRAINT ON (n:User) ASSERT n.uid IS UNIQUE;
CREATE CONSTRAINT ON (n:IP) ASSERT n.ip IS UNIQUE;
Use merge command to create nodes since this will ensure you do not create if it already exists.
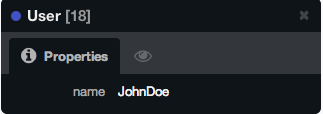
MERGE (u:User {uid:'JohnDoe'}) return u
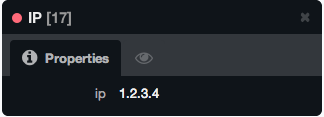
MERGE (i:IP {ip:'1.2.3.4'}) return i
Cypher statement to create WrongPasswordAttemept relation between existing IP address and user node.
MATCH (i:IP {ip:'1.2.3.4'}), (u:User {uid:'JohnDoe'})
MERGE (i)-[r:WrongPasswordAttempt {timestamp:timestamp(), weakPass:'Y'}]->(u)
Using Cypher Queries In Identifying The Attack In Progress
Query to identify number of failed login attempts in last 5 minutes from the ip (1.2.3.4)
MATCH (n:IP {ip:'1.2.3.4'})-[r:WrongPasswordAttempt]->(b)
WHERE r.timestamp > (timestamp() - 300000)
RETURN count(r)
Query to identify number of failed login attempts with weak password in last 5 minutes from the ip (1.2.3.4)
MATCH (n:IP {ip:'1.2.3.4'})-[r:WrongPasswordAttempt]->(b)
WHERE r.timestamp > (timestamp() - 300000) and r.weakPass='Y'
RETURN count(r) as WPACount
In above query following identification parameters are used.
- Value 300000 is equivalent to 5 mins in milliseconds.
- WPACount – is the Wrong Password Attempt count in 5 minutes duration
The time duration and number of failed attempts (WPACount) need to be analyzed based on application usage and load. In a ideal application it must be kept configurable value that can be modified at run time when needed.
This may sound trivial, however once your application is created your most time will be spent in analyzing and changing these parameters.
The attackers are typically using bots to launch brute force attacks and once they learn your detection speed them may reduce the speed to attack to stay below the radar.
Taking Action To Stop The Brute Force Attack
After the identification of attack action may become very obvious however you may want to choose it wisely and there may be multiple actions required.
- Temporary Blocking of IP Address The quickest way to stop attack will be to block the IP address from accessing you website. Permanently blocking the IP address may not be a good idea since it may be a common IP. Therefore you may also want to do the blocking for a time duration (lets say 1 day) and do more research on the IP address in mean time.
- Permanent Blocking of IP Address If the IP is constantly involved in such attacks you may want to block it permanently. To identify the IPs that are constantly involved in brute force attack you can run the query with a longer duration and notice the failed password attempt counts over a much longer period (lets say a week or a month)
- Further tuning the identification parameters. This may involved analyzing the speed of attack and changing the values for time duration and WPACount. You may want to increase or decrease these values based on your detailed research on the IP address and attack pattern.
- Resetting users that are compromised – This may sound weird, however once you have successfully identified an IP address that was doing brute force attack on your system you must also take action to gain the compromised users back. This can be done by looking at any successful login attempts by the client IP address in the attack duration. You must take some action to gain the accounts back from hackers. Some of the things you can do are
- Easiest way to do it will be resetting the password for user and notifying them with a change password link.
- Another way will be to lock the account and notify users to reset password and activate.
Scope For Improvement
This is just a preliminary setup for brute force attack detection. You may use same idea and improve on it to get better detection and accuracy. This design may lead to some false positives therefore a manual analysis is recommended before taking strong actions. The attackers are smart and they learn from your actions, therefore your system may need to be unpredictable and must be constantly tuned to detect and stop attacks.
Blocking the IP sounds like an obvious action however it may not always be the best choice if the attack is launched from common service providers like Amazon EC2 cloud. Blocking such IP may result in blocking many other good clients who are trying to reach you from same IP.
We have not accounted for IP Geo location information in this solution. May be a lot more complex and efficient detection can be done using Geo location identification. Lets say a user is typically accessing your website from USA. All of a sudden you notice a login from another country. This may be a sign of suspicious activity and you may want to take action on it. Such attack can be identified much faster if you have enough Geo information and user behavior details in your graph.
Summary
The recent decade has been full of security threats and attacks on websites and online products. With increasing computing power attackers have become really powerful. This makes job of a security professional even more difficult since we need to be constantly looking for ways to prevent our systems.
I hope you will find the article useful in stopping brute force attacks. Please share your thoughts and opinion on this.